Recently, CCID Consulting released the ChinaSafety big modelTechnology and Application Research Report (2023)”, the report draws a framework of China’s security big model, and conducts a comparative analysis of the main market players based on this framework.360With its outstanding technical capabilities and business layout, the security big modelTop of the chart,The company's comprehensive strength leads the industry.
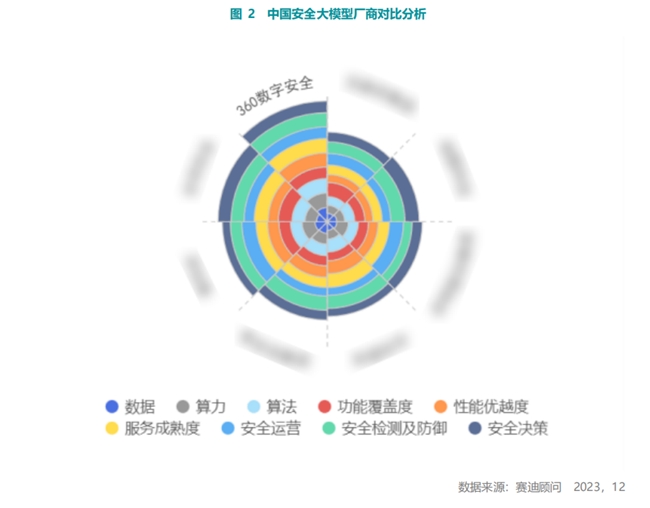
The report investigated360Digital Security, Ahnheng Information, Qi'anxin, Green Alliance Technology, Sangfor, Topsec, Venusstar, Knowsec, and other major domestic security big model manufacturers use a multi-level analysis framework to comprehensively evaluate the comprehensive strength of security big model manufacturers from three dimensions: technology, capability, and application.360The comprehensive capabilities of the safety large model ranked first.andIn the numberData and computing poweraspectPossess outstanding advantages.
360Big security model leads intelligent security services
As digital transformation deepens, digital technologies represented by big models are developing rapidly, bringing relatively rare challenges to the security field. Traditional security defense methods can no longer meet the needs of rapid response and emergency response. The report points out that with the emergence of big security models, the security industry is facing relatively rare opportunities and challenges.
In order to cope with new threats from the development of artificial intelligence, empower the process of digital transformation and intelligent improvement, and promote the digital development of the industry, 360 adheres to the strategy of "helping small and micro businesses in the mountains and the sea", implements the two main development lines of security and AI, and builds a natively secure general artificial intelligence large model 360 Smart Brain based on national-level security capabilities.Based on intelligent brain, we have created the firstImplementation AIPractical ApplicationSecurity industry big model——360Large safety model.

The report suggests that the architecture of the big model in the security industry can be divided into three levels: technology, capability, and application. The technology level focuses on the three core elements of the model: data, computing power, and algorithms. The capability level, based on the general big model, further expands the ability to understand specific tasks in the security field. The application level realizes specific applications in the field of network security by combining and expanding the underlying functions and algorithms. 360 Security Big Model is in a leading position at all levels, and ranks first in comprehensive data.
At the technical level, the 360 security big model is based on the 360 Intelligent Brain. It extracts high-quality corpus from the security big data such as attack and defense tactics, vulnerability database, virus database, etc. accumulated by 360 in the past 20 years for training. It uses big data, high computing power, and strong algorithms to create a moat barrier that is difficult to copy and has no replacement.
At the capability level, the security intelligence system built around the 360 security big model can provide capabilities such as target understanding, logical reasoning, effect evaluation, and knowledge memory, and support the connection, configuration, driving, and coordination of various products. Through the accurate calling of security tools, it can realize functions such as alarm analysis, attack link drawing, threat intelligence comparison, victim asset analysis, attacker attribution analysis, tracing, and security report generation.
At the application layer, the 360 Security Big Model fully leverages its generation capabilities and the practical experience of security experts to flexibly and adaptively orchestrate task plans and gradually form automated security operation capabilities. At present, it has broken through the difficult steps of scenarios such as automated threat hunting and automated security operations, and achieved scenario automation.
Large model + safety,Create AINew practical applications
The report pointed out that the security of big models themselves has attracted attention. The big model security capability framework built by 360 is based on the principles of "safety, goodness, trustworthiness, and controllability", and comprehensively guarantees the security of big models themselves with five major capabilities: training safety, operation safety, goodness of content, trust enhancement, and controllable framework.
The continuous improvement of the capabilities of the security big model will bring revolutionary changes to the industry and promote the development of new market space. CCID pointed out in the report that in the future, the security big model will accelerate the empowerment of existing security products, continue to promote intelligent security operations, and will be implemented in more security scenarios.
As a security big model for domestic AI practical applications, 360 Security Big Model enables the full product matrix, and can effectively and conveniently complete security problem consultation, situation indicator analysis, security incident processing, attack threat tracing, etc. In addition, 360 is based on the "small incision, deep" methodology, and uses "security scenario applicability" as an indicator to construct high-value security scenarios suitable for the characteristics of big models, and promote the implementation of security big models.
Since the release of version 1.0 in August 2023, the 360 Security Big Model has been undergoing training and optimization, while continuously improving the "AI content" of all 360 security products, making it the only company to realize the practical application of AI.