With the rapid development of artificial intelligence technology, related applications are entering every aspect of our lives. However, it also brings new challenges to the protection of personal information. At the National Cybersecurity Awareness Week 2024, which opened on the 8th, about theAI face-changingThe topic of personal privacy infringement, such as changing voices, has become the focus of attention. A "portrait photo", a close-up video of a person may become a new means and a new tool for criminals.
In this year's Network Security Expo, major security companies have demonstrated new products and technologies in the field of security, especially for the security of artificial intelligence has become the focus of major security companies.
The technicians in the picture are demonstrating the "AI face-swapping" technology, which requires only a static photo of the target character to make the character in the photo move.
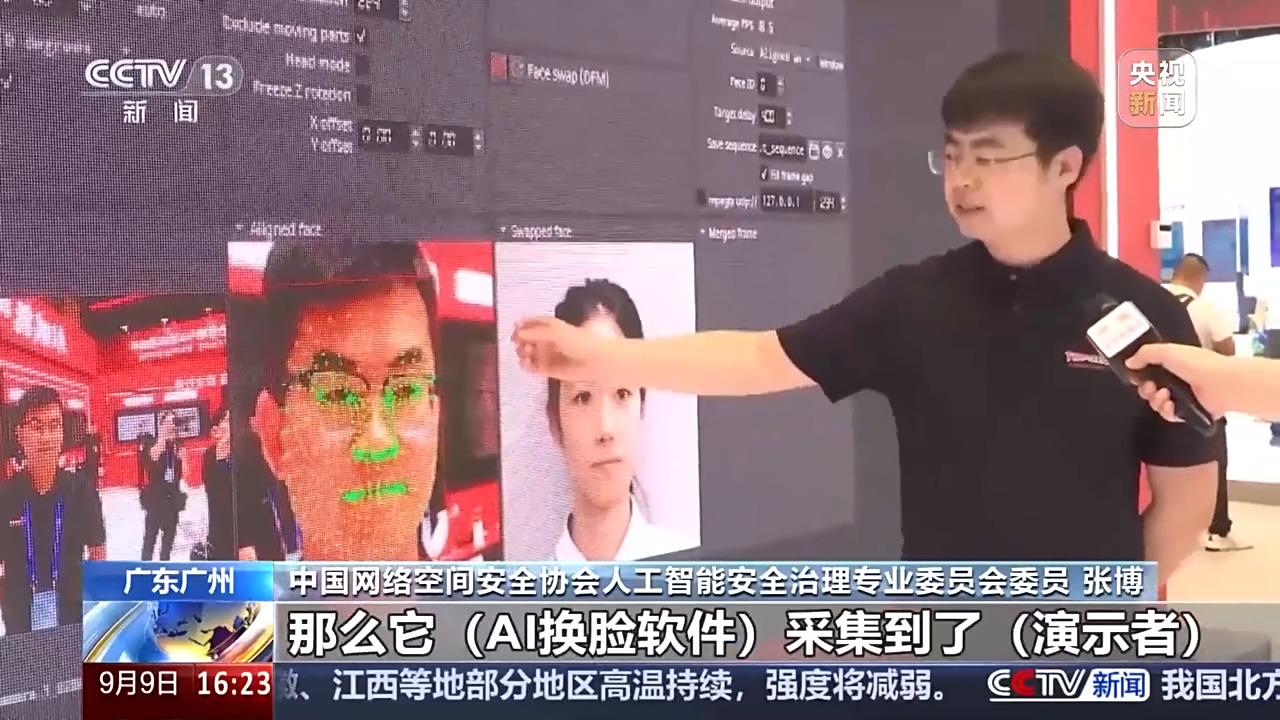
China Cyberspace Security Association Artificial Intelligence Security Governance Professional Committee member Zhang Bo: itself is a static picture will not move, the demonstrator to do some action, AI face changing software captured the demonstrator's facial features to move up, the characteristics of the fusion of the static picture, so that the picture according to the demonstrator's action moved, but also can be formed into a video.
Zhang Bo introduced, although now AI face change, voice change, etc. has a certain technical threshold and operating costs, but if the case is obtained by lawless elements, it may be used to impersonate others and implement related criminal activities.
China Cyberspace Security Association Artificial Intelligence Security Governance Professional Committee member Zhang Bo: The current AI face-swapping technology is still relatively mature, and it can support real-time face-swapping for video calls, which can achieve the degree of fakeness. In addition to changing the face, combined with changing the background environment, changing the voice, etc., the degree of realism will be higher, more difficult to distinguish.
Fake by face-swapping.indecent photograph
Extortion by lawless elements
AI face-swapping, voice-swapping and other technologies, once utilized by unscrupulous elements, can also become tools for extortion, and many such cases have already occurred around the world. Not long ago, Shenzhen police cracked down on a criminal gang that collected victim picture information from various channels such as the Internet, and then synthesized it for extortion and blackmail.
Not long ago, Shenzhen citizen Mr. Wu suddenly received an unfamiliar cell phone number sent by MMS, click to see it is actually him and a strange woman in a hotel room in the indecent photographs.

Mr. Wu: At that time I received a MMS, which is a nude photo of me. He was threatening me at the time, at what time before to contact him, transfer money, I was thinking wrong, the police.
Shenzhen police received the report, immediately on the clues provided by Mr. Wu to investigate. By combing through the records of the report, the police found that the city has the same encounter with more than just Mr. Wu, the suspects of extortion and blackmail are the same way.
With the depth of the investigation, the police found that this is a criminal gang headed by Wang Mou, a clear division of labor within the gang, someone is responsible for fixing the picture, someone is responsible for looking for targets, someone is responsible for texting and calling extortion. In possession of a large number of clues, Shenzhen police launched a unified net action, successfully arrested more than 10 suspects led by Wang.
In the suspect's computer, the police found a large number of indecent photos that had been synthesized with a face swap.
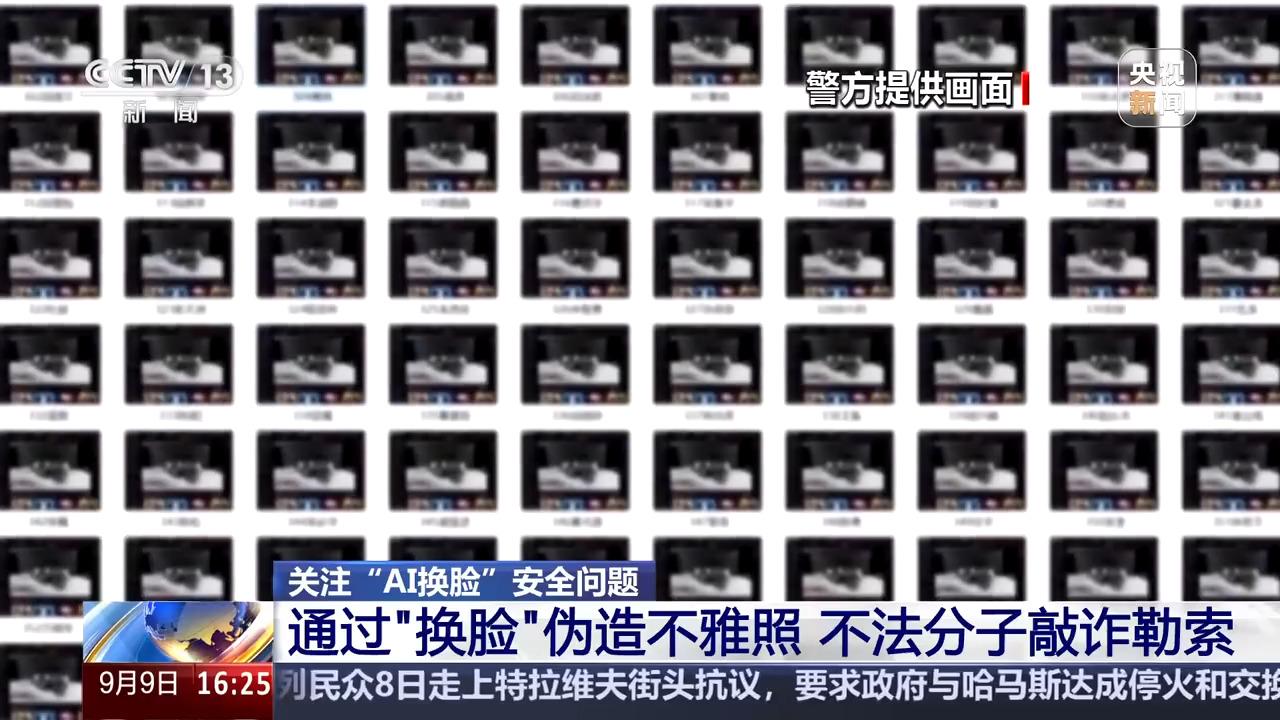
Shenzhen Municipal Public Security Bureau Pingshan Branch police Zhang Wei: from the suspect's computer inside the extraction of relevant evidence, these pictures are suspects from a variety of channels to collect the victim picture information, and then synthesized to be used to extort the victim.
At present, Wang and others have been prosecuted by the procuratorial authorities. The case is under further trial.
Experts: accelerating the development and application of relevant countermeasure technologies
The use of advanced AI technology to produce face-swapped videos or simulated voices for illegal activities is indeed easy to fool people, which not only poses new challenges to the protection of personal privacy, but also highlights the importance of relevant regulations and countermeasure technologies.
It is understood that at present, the "AI face-swapping" technology for the implementation of various types of personal information infringement has occurred from time to time, in the gray area and even illegal and criminal areas are abused. Network security experts suggest that the development and application of relevant countermeasure technologies should be accelerated.
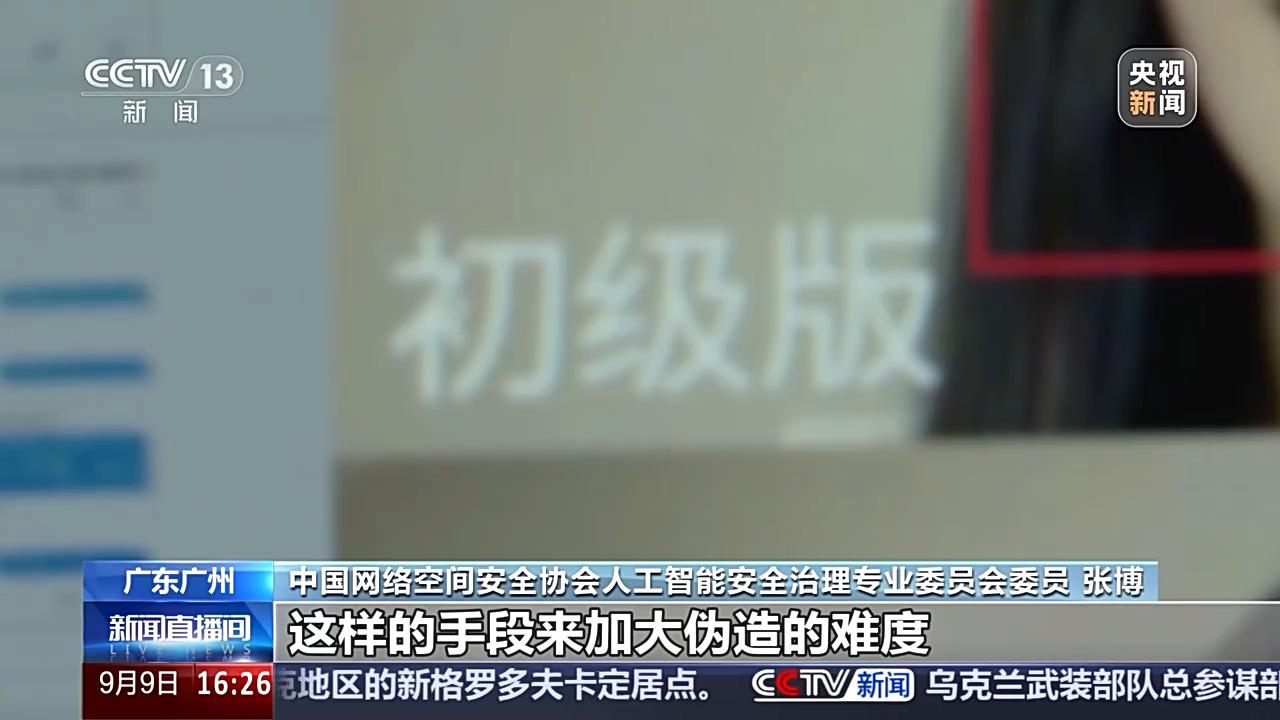
Zhang Bo, member of the Artificial Intelligence Security Governance Professional Committee of the China Cyberspace Security Association: The authenticity of the video can be recognized through artificial intelligence detection technology, whether there is forged content. In addition, it can also be combined with the means of identity authentication and digital watermarking to increase the difficulty of forgery. From the management side, it is necessary to accelerate the formulation and implementation of relevant laws and regulations as well as regulatory measures to standardize the use of AI applications and application scenarios.
Cybersecurity experts suggest that the most crucial reason for illegal behaviors such as AI face swapping is the leakage of personal privacy information. Therefore, we should try to avoid excessive disclosure and sharing of personal bio-information such as face and fingerprints in our daily online activities. If you receive a video of a family member or leader transferring money or making a remittance, be sure to check the authenticity of the video carefully.
China Cyberspace Security Association Artificial Intelligence Security Governance Professional Committee member Zhang Bo: AI face-switching is usually accompanied by transaction fraud scenarios, such as video calls, pay attention to observe the other party's facial contours in the video, the light background and such details, to see if there is any abnormality. If necessary, you can ask the other party to do a quick look up, nod, turn the head of the action, to further determine whether the video has abnormal details, to confirm that the video is real.
Vigilance! Don't post these kinds of photos!
In daily life, many people like to sunshine food and beautiful scenery on the circle of friends and short videos, but if you are not careful, these behaviors are likely to indirectly leak your personal information. If obtained by people with ulterior motives, they may jeopardize the property and even personal safety of yourself and your family. Which photos must be careful and never posted online?
Do not publish hand-held ID cards or hand-held white paper photos. These photos will contain sensitive information such as personal name, ID number, address, etc. Once leaked, lawbreakers may use this information for identity theft, financial services such as credit cards, loans, etc., or even illegal activities. In addition, photographs such as hand-held white paper or hand-held newspaper are often used to verify identity, and if obtained by lawless elements, they may be used to produce false documents or conduct network fraud, which will bring economic losses and damage to the reputation of individuals.
Don't post photos of all kinds of tickets. Many people on business trips and travel like to take pictures of train tickets or airplane boarding passes and send them to their circle of friends to share. These tickets will not only contain information such as name, origin, destination, etc., but will also contain passengers' personal information in the stripe code or QR code, which has the possibility of being cracked and stolen by lawless elements.
Do not post photos of house keys, license plates, etc. By using technical means such as big data, the unscrupulous person will analyze the specific location of the publisher at a specific time through these photos, and will also obtain the publisher's relevant living habits. Therefore, it is best not to show items with distinctive features, such as house keys, license plate numbers, etc., in your photos.
Cybersecurity experts emphasize that protecting personal privacy is of paramount importance. The public should be vigilant and avoid posting photos containing sensitive personal information freely on the Internet. It is also recommended to regularly check and update personal privacy settings to ensure the security of personal information.